Use of In Silico Methods to Study Crime
By Thomas J. Dover, Ph.D

The offender is on the way home from work when his violent fantasies become overwhelming. He decides to go to a prostitute stroll that he has frequented in the past. In fact, he has abducted and killed women two other times from this area. After he finds a new suitable target, he gets her into his car, where he can control her. However, he feels too exposed to act out his fantasies because there are too many people around. Instead, he drives the woman to a secluded area outside of town where he kills her, dumps her body next to a creek, and then goes home.
By the time this series of murders ends, the offender has successfully abducted six victims. Five are killed and dumped in the same general area, and one has escaped.
In this simulation, the offender occupies a computational version of reality. His motivational drivers can be tweaked to create various violent and nonviolent outcomes. With current and emerging computational resources, running this simulation can produce hundreds of different outcomes in minutes and provide the law enforcement community with a means to observe and better understand these types of behaviors and events (see sidebar 1).
This simulation is an example of an in silico method that can be used to study violent crime. The term in silico refers to the use of computer models to create a virtual laboratory1 and is a “generative” method of scientific inquiry. This means that in silico methods are informed by real-world systems but can be effectively used to “generate” data for further examination. While used by professionals in the physical and biological sciences for decades, these methods are relatively new to the social and cognitive sciences. When applied to the study of crime and law enforcement, in silico methods can be used to augment and test the understanding of decision-making, criminal behavior, and crime patterns while watching complex interactions unfold. This can include “priming,” “goal setting,” “interest,” or other cognitive or social factors often hidden from practical observation in the real world.

Dr. Dover serves as a crime analyst with the FBI’s Behavioral Analysis Unit-5 and instructs on topics pertaining to behavioral analysis for the FBI National Academy.
This can be done without violating ethical standards, harming the community, or putting potential victims at risk. In addition, in silico assumptions can be relatively easy to review, test, and compare with reality.
Simulation
Human beings naturally engage in implicit mental simulations. They constantly build and test their own mental models to define the environment and people in it. These schemas, scripts, and internal narratives act as road maps to help people spatially and socially navigate both routine and novel situations. For instance, while in a traffic jam, individuals might mentally review and consider various alternate routes. During a meeting, they may self-censor a comment that could result in negative consequences.
To form their expectations, people think about and, thereby, informally model what they currently know and then make inferences. Investigators do this regularly when they develop crime theories or consider an offender’s potential motives. These expectations, drawn from mental simulations, constitute an important part of understanding the past, reacting to the present, and planning for the future while dealing with the unknown.
Intellectually considering possibilities and using computer simulations have remarkable similarities. In both cases, people draw from experience and research to construct meaning for what they are trying to understand. A simulation simply serves as an analogy for reality that can provide unique or unexpected insights.
Useful Models
Models are static representations of the rules that turn a series of inputs into a series of outputs. For instance, an implicit version of the routine activities theory (RAT) suggests that criminal activity occurs when a motivated offender encounters an available target in the absence of capable guardianship.2 These relationships can be expressed explicitly as a set of rules, or a model. The more explicitly the model is expressed, the more practically it can be tested and used to address specific issues through simulation.
While a model defines how inputs will interact, simulation involves a dynamic test of what emerges from these interactions. Using an analogy, when someone builds a paper airplane, the person has created a model. Throwing it creates a simulation that allows the individual to see how the model performs (e.g., flies straight, curves, crashes). Likewise, a simulation based on the RAT model involves a dynamic representation of the components (e.g., motivated offenders, available targets, capable guardianship) and what patterns emerge over time when they follow rules of interaction.
To further illustrate the usefulness of in silico methodology, burglaries can be explored by expanding on the RAT model (see figure 1). To begin, RAT can be expressed as an agent-based model (ABM) of burglaries with a simple set of rules.3
- If a burglar encounters a residence without the presence of police, a burglary will occur.
- If a burglar encounters a residence with the presence of police, a burglary will not occur.
“When applied to…crime and law enforcement, in silico methods can be used to augment and test the understanding of decision-making, criminal behavior, and crime patterns while watching complex interactions unfold.”
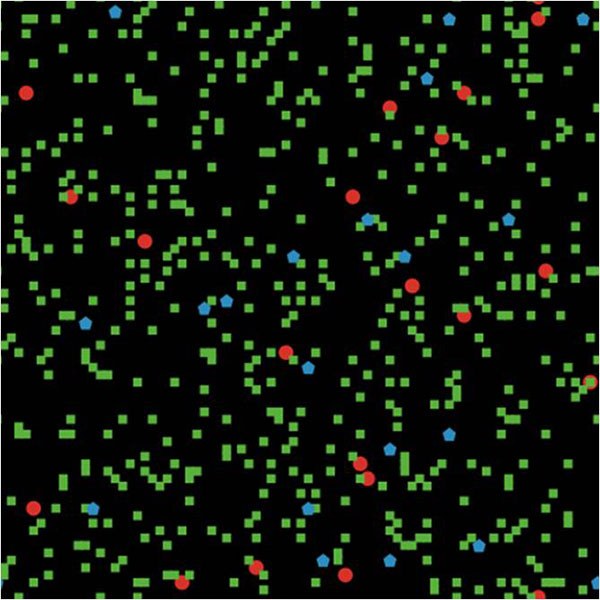
Figure 1: An in silico implementation of the routine activities theory (RAT) in one community.
For instance, the model in figure 1 includes 20 burglars, 500 residences, and 20 police officers.4 Running this model in a simulation once may prove informative. However, running it multiple times and within different virtual communities5 provides more understanding of the model dynamics across these virtual communities (see figure 2).
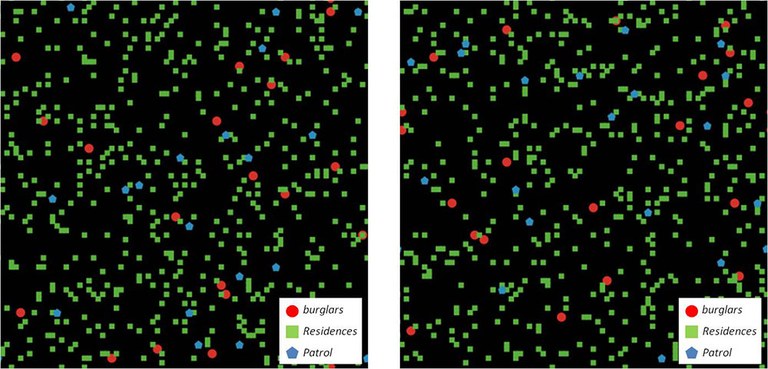
Figure 2: An in silico implementation of the routine actions theory (RAT) in two different virtual communities.
As an example, running the simulation for 100 virtual communities6 results in an average within those communities of—
- 304 burglaries committed;7 and
- 0 burglaries prevented.
In this simulation, the police are not preventing burglaries. According to the model, the burglar and police officer must be at the same residence simultaneously for police presence to prevent a burglary. This is not a realistic assumption. However, it does lead to an interesting question: What is it about police presence that theoretically will prevent a burglary? An important part of prevention involves making the criminal activity riskier for the offender. If the presence of police increases this risk, then the observable presence of police in the area should make an offender think twice about committing a burglary.
Accordingly, giving a burglar the ability to see police from afar (roughly 300 feet) and rerunning the simulation across the same 100 virtual communities results in an average of—
- 114 burglaries committed;8 and
- 189 burglaries prevented.9
With the burglar’s ability to see police at a distance added, a burglar makes the conscious decision not to commit a burglary because he saw police in the area approximately 189 times (during each simulation run).
This represents a 62.5 percent reduction in burglaries; however, 114 burglaries still is a relatively high number. What happens if unmarked units are in the area not to have a deterrence effect, but instead to observe and interdict when a burglary occurs? An adjustment to the model can make burglars oblivious to police presence and give police the ability to see burglars from roughly 300 feet away. In addition, when police observe a burglary and interdict, the model can be set so that they are able to follow up the interdiction with an arrest (removal of the burglar from the simulation) 50 percent of the time. Running this new configuration across the same 100 virtual communities results in an average of—
- 66 burglaries committed,10 of which 39 resulted in interdiction;11 and
- 238 burglaries indirectly prevented.12
Given that the same 100 virtual communities were used and there was an average of 304 burglaries committed in each community in the initial baseline, it now can be said that with the application of interdiction that potential burglars never were given the opportunity to commit 238 of those 304 burglaries because they already had been arrested and removed from the equation. The model has created an alternative future for each of the virtual communities.
A logical follow-up question to these two different model revisions is, what if both deterrence and interdiction are part of the same strategy? To answer this question, the model can be set to include both deterrence (the burglar sees police if within 150 feet) and interdiction (police detect the burglar if within 300 feet). Running this revision across all 100 virtual communities results in an average of—
- 77 burglaries committed,13 of which 38 resulted in interdiction;14 and
- 248 burglaries prevented.15
The 248 prevented burglaries fall into two categories—those stopped by deterrence (21 times)16 and burglaries indirectly prevented because of interdiction and arrest (227 times).17
The important takeaway from each of these simulations is how consistently the numbers change across the 100 virtual communities given the parameter changes.
Real-World Applicability
The results from the above burglary model may not immediately transfer to the real world due to factors that the model does not account for, such as actual street layout, differing levels of offender motivation, and the presence of target hardening. In fact, a common criticism of some in silico methods is that simple models do not offer a level of complexity useful or applicable to real-world scenarios or circumstances. However, even a simple model with subsequent simulation can become a powerful tool by illustrating useful outcomes and posing relevant questions.
For instance, given the aggregated results of the burglary model, it is interesting to note that the combination of interdiction and deterrence actually results in a higher average number of burglaries than interdiction alone. Upon further reflection, this unexpected result does make sense. If burglars have an opportunity to avoid interdiction by observing that there are police in the area, they simply defer their activity until the police leave. These burglaries have not been prevented, just delayed.
This point derived from the burglary model highlights a deeper issue—capable guardianship is not always a permanent deterrent. Police presence alone does not reduce the motivation for burglary in the long term. On the other hand, while interdiction and arrest may not affect motivation, they do diminish opportunity.
Even this simple burglary model and simulation can provide a foundation for additional complexity. Simple changes may lead to powerful and interesting observations. For instance, with relatively little effort, the burglary model could be modified to include a depiction of burglars with diverse and dynamic motivations based on factors like age, drug use, time of day, or even level of “thrill” involved. Adding more specific geospatial and temporal features also could help an agency understand how the factors in the model might play out in their own jurisdiction.
One reason for using simulations in law enforcement is that it encourages problem-solving by allowing users to make mistakes and see the potential consequences of those mistakes in a safe environment. This explains why simulation has gained a foothold in training. The use of live scenarios, shooting simulators, and driving simulators gives trainees the opportunity to test their assumptions and adjust based on simulation feedback.
A “test-retest-decide” methodology in silico can benefit operational anticipation and planning by allowing an agency to define and refine intended consequences and foresee and mitigate potential unintended ones. This can be applied at a variety of scales within a law enforcement environment, from administrative policy to strategic initiatives.
Within behavioral analysis, in silico techniques provide an opportunity to create artificial populations of offenders, especially in low-base-rate events like serial homicide. The reason to generate these populations is not to predict any specific offender’s actions or behaviors, but rather to test theories about offending.
“…even a simple model with subsequent simulation can become a powerful tool by illustrating useful outcomes and posing relevant questions.”
Agencies can identify their own complex issues that may benefit from being addressed in silico. For instance, traffic enforcement represents one of the biggest challenges facing many police departments. In these instances, implementing a traffic simulation could foster a complex understanding of vehicle flow at problematic intersections, identify and address roadways with high accident rates, or even help plan for traffic issues that emerge during large-scale entertainment or sporting events.
Many other potential applications of in silico methods exist. A few examples serve to demonstrate.
- Creating a system dynamics (SD) model18 of an agency and then stressing it can test the resilience of the organization’s structure when two or more major events occur simultaneously.
- Using an ABM19 might help a correctional facility anticipate the point at which a riot may emerge from inmate and correctional staff interactions.
- Employing a social network analysis (SNA) model20 to simulate a criminal organization’s network of actors, skill sets, and assets may facilitate predicting that organization’s reaction to the elimination of an income stream. Does the group become crippled, refocus on a different income source, or become more violent and territorial?
Countless complex subjects exist that, although ripe for analysis, are difficult to measure and observe or do not allow for the ethical collection of data. Understandably, police executives in the real world do not want to stress their agency to see what breaks it, correctional facilities do not want to incite a riot, and many interdiction efforts can have a wide range of costly unintended consequences.
Resources
Modeling and simulation resources can take on a variety of scales and costs. However, in silico methods can help conserve resources and reduce expenditures overall. As such, in silico efforts depend on the 1) specific need and 2) human expertise available to engage in the project.
To the first point, it is surprising what someone can accomplish using a simple spreadsheet, especially when implementing an SD model. Even so, more specialized models, like ABMs or SNAs, can be created with either open source or relatively inexpensive software.21
Regarding the second point, when engaging in an in silico effort, it is most important to involve personnel who can create a model quickly and efficiently and employ it in an explicit and collaborative way. This requires individuals willing to be creative and push the boundaries of software suites that many departments already have in place.22
Agencies also may have access to outside sources of expertise. For instance, local or state planning departments may be using simulations for traffic planning or infrastructure development and could serve as a potential source of expertise. Further, agencies might want to consider reaching out to local universities and research centers that have strong computational modeling, simulation, or computer science departments.
“Agencies can identify their own complex issues that may benefit from being addressed in silico.”
Sidebar 1
Integrated Synthetic Offender Model
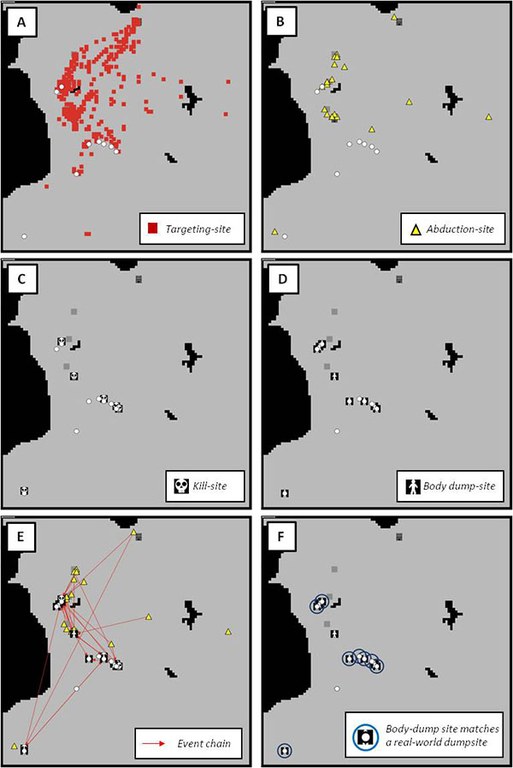
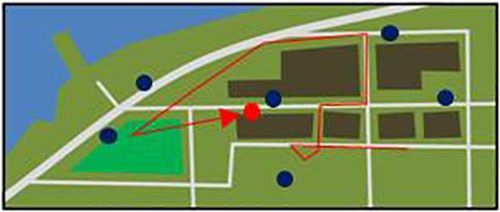
The integrated synthetic offender (ISO) model displays geospatial sites associated with a simulated serial offender.23 These features emerge from the complex overlay of the offender’s “need”-driven goals and his opportunities to offend. Over time, this artificial offender may develop violent fantasies, interact with potential victims (A), attempt to abduct and control some of those victims (B), and even commit homicide (C) and dump the victim’s body (D). These sites can be analyzed by looking at event sequences (E) and comparing sites to a known real-world series of events (F).
These panels represent only one run of the ISO model. However, if this simulation is run hundreds of times, each will represent an offender that will create unique behavioral and geospatial patterns. This model can be used to better understand how offender affect and goal-setting translates to adaptation and geospatial patterns to better inform the investigation of real-world series.
Sidebar 2
A Variety of Models
Computational models and simulations can be applied in many different variations, scales, and levels of formalization.24 Each type of model offers a different way to view real-world systems and provide insights. Three different models that can be useful in addressing real-world law enforcement questions are agent-based models (ABMs), system dynamics (SD) models, and social network analysis (SNA) models.
Agent-Based Models
A relatively simple agent-based model (ABM) may only involve the interactions of different agents. (illustrative only)
More complex agent-based models (ABMs) might show how agents interact in a defined geospatial environment. (illustration only)
ABMs are used to represent autonomous entities (called agents) within a system and show how their actions and interactions evolve over time. This type of model is ideal for demonstrating interactions among people, organizations, or communities.
One of the significant outcomes of an ABM is the emergence of systemwide effects generated from relatively simple interactions of the agents. The burglary model from this article is an example of an ABM in which burglars, residences, and police can be represented by different types of interacting agents. The ISO model (from sidebar 1) uses an ABM to represent the offender’s geospatial activities in a virtual environment.25 Other modeling and simulation efforts involving ABMs have been used more strategically to illustrate general geospatial offending patterns26 and explore criminal hot spots.27
System Dynamics Models
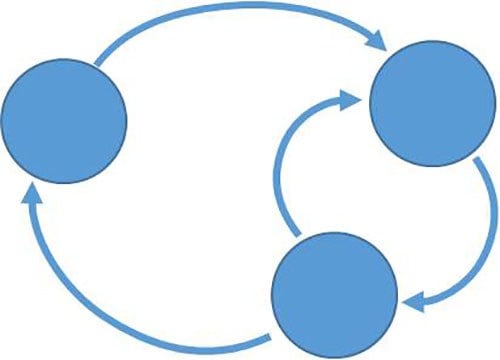
A system dynamics (SD) model can be expressed as a simple casual loop diagram.
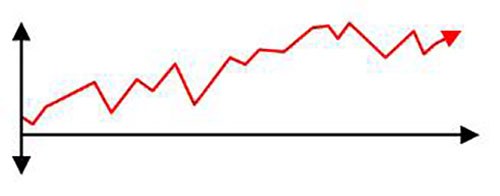
A system dynamics (SD) model can be expressed as an accumulation of a resource of affect. (illustrative only)
SD models focus on feed-back and feed-forward within a system. Often, they involve a number of components and dynamic changes from one system state to another. These models can be visualized using causal loops or flow diagrams. They can prove effective at representing allocation of defined resources and other economically based systems.
For instance, the flow of resources within a law enforcement agency or the distribution of drug proceeds within a criminal enterprise would represent ideal subjects for an SD model. These models also prove effective in examining threshold-based activities and behaviors and, therefore, can be used to represent nontangible things that accumulate, like affect and morale. As an example, the ISO model uses an SD to represent the offender’s rising and falling interest in offending.28 SD models also have been used to represent rising and falling disgruntlement and its potential contribution to insider threat.29
Social Network Analysis Models
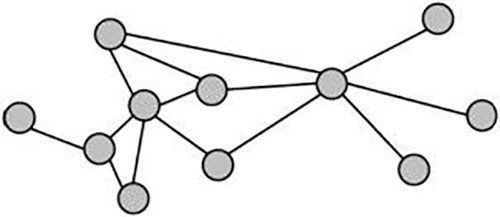
A social network analysis (SNA) model generally is expressed as a series of nodes connected by lines or edges that contain connection information and define interconnectedness between nodes.
SNA models use graph theory to represent entities as nodes with interconnected relationships symbolized by lines (or edges). These models generally are expressed as graphs that commonly resemble link charts. Although the use of networks to signify connections between people, places, and things has existed for a long time,30 the application of SNA in silico greatly has increased the utility of this type of modeling. The lines between nodes can represent a significant amount of dynamic information and can be applied to highly complex and multidimensional problems.
SNA can be especially useful in representing and analyzing criminal connectivity. Several SNA models have been used to analyze terrorist organizations,31 even going so far as to develop dynamic simulations to understand how terrorist networks repair themselves and persist in light of interdiction efforts.32
Conclusion
A model or simulation is only as good as its weakest assumptions and no model—in silico or otherwise—can account for all factors that define a problem. Moreover, models and simulations never should be trusted to tell the whole story. However, when a model is explicitly implemented in silico, users can view it outside of themselves, where they can refine it; correct it; and, ideally, agree on its purpose and usefulness.
In silico methods do not involve risk to personnel or the community because they shift threats to life and property into a virtual world, where they are a matter of 1s and 0s. These methods reduce the necessary resources to make interesting and powerful observations and have the potential to increase the efficient use of real-world resources. Ultimately, in silico methods are meant to be shared and provide a means to test assumptions and open minds through collaboration.
Dr. Dover can be reached at tjdover@fbi.gov.
Endnotes
1 The term in silico first was used by mathematician Pedro Miramontes during the 1989 workshop “Cellular Automata: Theory and Applications” in Los Alamos, New Mexico, where he presented on the use of computational methods to study molecular evolution.
2 Lawrence E. Cohen and Marcus Felson, “Social Change and Crime Rate Trends: A Routine Activities Approach,” American Sociological Review 44, no. 4 (August 1979): 588-608, accessed September 30, 2019, https://www.jstor.org/stable/2094589?seq=1#page_scan_tab_contents.
3 For a detailed description of ABMs, see sidebar 2.
4 This model was created by the author using NetLogo 5.0.3 software. For additional information, see “NetLogo,” Center for Connected Learning and Computer-Based Modeling, Northwestern University, https://ccl.northwestern.edu/netlogo/index.shtml. The model and simulation outputs are presented for illustration purposes only.
5 A random seed value provides a base number for the random distribution of agents in the model. This will cascade through all random functions in a simulation. Using the same random seed value for the simulation would show how variations of the model perform in the same virtual community. Running variations within the same virtual community and transferring those variations to different virtual communities can be automated in the burglary model. The results of running this simulation within multiple virtual communities then can be reported as averages (with standard deviations), and general trends can be assessed.
6 The model is run for 200 recalculations.
7 One standard deviation (1 SD): ±18
8 1 SD: ±12
9 1 SD: ±16
10 1 SD: ±13
11 1 SD: ±6
12 1 SD: ±21
13 1 SD: ±15
14 1 SD: ±6
15 1 SD: ±31
16 1 SD: ±7
17 1 SD: ±25
18 See sidebar 2.
19 Ibid.
20 Ibid.
21 For instance, the ISO model from sidebar 1 was built using open-source software.
22 Especially database or spreadsheet solutions already in use by the department.
23 Thomas J. Dover, “Implementing a Complex Social Simulation of the Violent Offending Process: The Promise of a Synthetic Offender” (Ph.D. diss., George Mason University, 2016).
24 For a complete discussion of computational models see Claudio Cioffi-Revilla, Introduction to Computational Social Science: Principles and Applications (London: Springer-Verlag, 2014). Additionally, for an introduction to some useful computational methodologies tested in insider threat research, see Andrew P. Moore, Kirk A. Kennedy, and Thomas J. Dover, “Introduction to the Special Issue on Insider Threat Modeling and Simulation,” Computational and Mathematical Organization Theory 22, no. 3 (September 2016): 261-272; this discussion includes Game Theory models and Bayesian Belief Networks, neither of which are described in the article.
25 The ISO model also uses a second set of ABMs to represent the offender’s perception of the virtual environment and his own conceptual simulation of solutions during tactical planning and adaptation. See Dover, “Implementing a Complex Social Simulation of the Violent Offending Process.”
26 Lin Liu, Artificial Crime Analysis Systems: Using Computer Simulations and Geographic Information Systems, eds. Lin Liu and John Eck (Hershey, PA: Information Science Reference, 2008); Nicolas Malleson, “Using Agent-Based Models to Simulate Crime,” in Agent-Based Models of Geographical Systems, eds. Alison J. Heppenstall et al. (Berlin: Springer, 2012); and Nick Malleson et al., “Using an Agent-based Crime Simulation to Predict the Effects of Urban Regeneration on Individual Household Burglary Risk,” Environment and Planning B: Planning and Design 40, no. 3 (2013): 405-426, accessed October 3, 2019, https://journals.sagepub.com/doi/10.1068/b38057.
27 Elizabeth R. Groff, “‘Situating’ Simulation to Model Human Spatio-Temporal Interactions: An Example Using Crime Events,” Transactions in GIS 11, no. 4 (August 2007): 507- 530, accessed October 3, 2019, https://onlinelibrary.wiley.com/doi/abs/10.1111/j.1467671.2007.01058.x; and Tibor Bosse and Charlotte Gerritsen, “Agent-Based Simulation of the Spatial Dynamics of Crime: On the Interplay Between Criminal Hot Spots and Reputation” in Proceedings of the 7th International Conference on Autonomous Agents and Multi Agent Systems, vol. 2 (Richland, SC: International Foundation for Autonomous Agents and Multiagent Systems, 2008): 1129-1136, accessed October 3, 2019, https://www.cs.vu.nl/~tbosse/papers/AAMAS08_crim.pdf.
28 In the ISO model, an SD accumulator model is used to track and define the affective state of the offender.
29 John A. Sokolowski, Catherine M. Banks, and Thomas J. Dover, “An Agent-Based Approach to Modeling Insider Threat,” Computational and Mathematical Organization Theory 22, no. 3 (September 2016): 273-287, accessed October 7, 2019, https://link.springer.com/article/10.1007/s10588-016-9220-6.
30 Moore, Kennedy, and Dover.
31 Arie Perliger and Ami Pedahzur, “Social Network Analysis in the Study of Terrorism and Political Violence,” PS: Political Science and Politics 44, no. 1 (January 2011): 45-50, accessed October 7, 2019, https://pdfs.semanticscholar.org/258b/3f89469ebb569f5ae3d551c8176aeb831557.pdf; and Steve Ressler, “Social Network Analysis as an Approach to Combat Terrorism: Past, Present, and Future Research,” Homeland Security Affairs 2 (July 2006), accessed October 7, 2019, https://www.hsaj.org/articles/171.
32 Maksim Tsvetovat and Maciej Latek, “Dynamics of Agent Organizations: Application to Modeling Irregular Warfare,” in Multi-Agent-Based Simulation IX: International Workshop, MABS 2008, Estoril, Portugal, May 2008—Revised Selected Papers, eds. Nuno David and Jaime Simao Sichman (Heidelberg, Germany: Springer-Verlag, 2009), 60-70.
